Secure API integration is crucial for modern applications. It ensures safe data exchange and prevents unauthorized access, a vital aspect for any application in today’s digital landscape. This guide delves into various aspects of secure API integration, from authentication and authorization to data security and monitoring, covering different environments and best practices.
This comprehensive guide will cover everything from the fundamentals of secure API integration to advanced topics like microservices architecture. We’ll explore essential concepts like authentication mechanisms, data protection, rate limiting, and secure design principles. Furthermore, we’ll discuss the best practices for implementation across diverse environments, including cloud, on-premise, and hybrid setups.
Introduction to Secure API Integration
Secure API integration is the process of connecting applications through Application Programming Interfaces (APIs) in a way that safeguards sensitive data and prevents unauthorized access. This involves implementing robust security measures at every stage of the integration process, from API design and development to deployment and maintenance. The goal is to ensure the integrity, confidentiality, and availability of data exchanged between applications.Modern applications rely heavily on APIs for seamless communication and data exchange.
This interconnectedness necessitates robust security protocols to protect sensitive information, prevent malicious attacks, and maintain user trust. In a world increasingly reliant on digital services, secure API integration is no longer a luxury but a fundamental requirement for ensuring the safety and reliability of applications.
Potential Consequences of Insecure API Integration
Insecure API integration can have significant repercussions for businesses and users. Compromised APIs can lead to data breaches, financial losses, reputational damage, and legal liabilities. Unauthorized access to sensitive information can result in identity theft, financial fraud, and other serious security risks. The impact of a breach can extend beyond the immediate victims, potentially affecting the entire ecosystem of interconnected applications.
Key Benefits of Implementing Secure API Integration Practices
Implementing secure API integration practices provides several key benefits. These include enhanced data protection, improved application reliability, reduced security risks, and increased user trust. Strong security measures minimize the risk of data breaches, ensuring the confidentiality and integrity of sensitive information. Robust authentication and authorization mechanisms strengthen application security, preventing unauthorized access and misuse.
Different API Integration Approaches
Various approaches exist for integrating APIs, each with its own strengths and weaknesses. A crucial factor in choosing an approach is the level of security required and the specific needs of the application. Common approaches include direct API calls, using API gateways, and utilizing message queues. Each approach has unique implications for security, and careful consideration must be given to ensure appropriate security controls are in place.
- Direct API Calls: This method involves directly invoking the API endpoints. While straightforward, it can lack centralized control and management, potentially exposing the application to vulnerabilities if not implemented securely. This approach requires careful configuration of security protocols, such as authentication and authorization mechanisms.
- API Gateways: An API gateway acts as a central point of entry for all API requests. It provides a layer of abstraction, allowing for centralized security enforcement, rate limiting, and other security controls. This approach strengthens security by centralizing security policies, making management easier.
- Message Queues: Message queues decouple applications, allowing for asynchronous communication. This decoupling can improve scalability and reliability. Security measures should be integrated into the message queue infrastructure to protect data during transmission and storage.
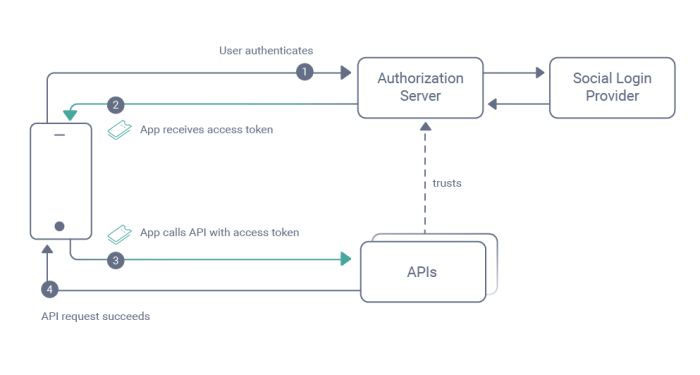
Authentication and Authorization Mechanisms

Securing API access is paramount for protecting sensitive data and maintaining system integrity. Robust authentication and authorization mechanisms are critical components of this process. These mechanisms verify the identity of API clients and restrict access to specific resources based on predefined rules. This section delves into various authentication methods, role-based access control, strong password policies, and the role of API gateways in enforcing security.Implementing secure authentication and authorization is crucial to mitigate risks such as unauthorized access, data breaches, and service disruptions.
A well-designed system ensures only legitimate users can interact with the API, preventing malicious actors from exploiting vulnerabilities.
Authentication Methods for Secure API Access
Various methods exist to authenticate API requests. Choosing the appropriate method depends on factors like the level of security required and the complexity of the system. Common methods include API keys, OAuth 2.0, and JSON Web Tokens (JWTs).
- API Keys: A simple, widely used method where each client is assigned a unique key. The key is sent with each request, and the server verifies its validity. This approach is straightforward to implement but lacks the flexibility of more sophisticated methods like OAuth 2.0.
- OAuth 2.0: A more complex but powerful framework for authorization. It allows clients to access protected resources on behalf of the resource owner. It involves multiple steps including authorization grants and token exchange, offering enhanced security and user control over access. It’s commonly used for web applications and mobile apps.
- JSON Web Tokens (JWTs): JWTs are compact, self-contained JSON packages that can be securely transmitted between parties. They include information about the client, the resource, and the time of access, facilitating secure and efficient communication. They are widely used for their ease of use and efficiency, especially for systems requiring stateless authentication.
Role-Based Access Control (RBAC) for APIs
Role-based access control (RBAC) is a method for managing access to resources based on roles assigned to users. This approach defines roles with specific permissions and assigns users to those roles, thereby controlling their access to API endpoints.
- Defining Roles: Roles are pre-defined sets of permissions for accessing resources and functionalities within the API. A “viewer” role might have limited access, while an “administrator” role has broader capabilities.
- Assigning Roles to Users: Administrators assign users to specific roles, controlling their access based on these roles. This ensures only authorized users can perform specific tasks.
- Defining Permissions: Permissions specify the actions a user with a given role can perform on different resources within the API. For example, a “viewer” role might have permission to read data but not to modify it.
Strong Password Policies for API Credentials
Robust password policies are essential for safeguarding API credentials. Weak passwords can be easily compromised, leading to security breaches.
- Minimum Length: Passwords should meet minimum length requirements, incorporating a mix of uppercase and lowercase letters, numbers, and symbols.
- Complexity: Enforcing complexity requirements for API credentials enhances security significantly.
- Regular Updates: Periodic password updates are essential to prevent persistent breaches.
Comparison of Authentication Methods
| Authentication Method | Strengths | Weaknesses |
|---|---|---|
| API Keys | Simple to implement, fast | Limited flexibility, no user management |
| OAuth 2.0 | Robust, secure, user-centric | More complex to implement |
| JWT | Efficient, stateless, secure | Requires careful token management |
Using API Gateways for Authentication and Authorization
API gateways act as a central point for managing API requests, including authentication and authorization. They can enforce policies across multiple APIs, improving security and streamlining operations.
- Centralized Authentication: Gateways handle authentication for all APIs, reducing the burden on individual services.
- Policy Enforcement: Gateways enforce access control policies, preventing unauthorized access.
- Rate Limiting: Gateways can implement rate limiting to prevent abuse and protect APIs from overload.
Data Security and Protection
Protecting sensitive data exchanged through APIs is paramount. Robust security measures are essential to safeguard user information and maintain the integrity of the system. This section details crucial aspects of data security, encompassing encryption, validation, secure coding, and data masking techniques.Data breaches can have severe consequences, ranging from financial losses to reputational damage and legal liabilities. Implementing comprehensive security protocols is therefore a critical component of API design and development.
Data Encryption at Rest and in Transit
Ensuring data confidentiality is paramount, both when stored (at rest) and during transmission (in transit). Encryption transforms readable data into an unreadable format, preventing unauthorized access. Encryption at rest protects data stored in databases or on file systems, while encryption in transit safeguards data during transmission across networks.
Secure Data Transfer Protocols
Secure communication channels are crucial for preventing unauthorized access to data during transmission. HTTPS (Hypertext Transfer Protocol Secure) is a standard protocol that utilizes encryption to protect data exchanged between clients and servers. HTTPS encrypts the communication channel, making it significantly more difficult for attackers to intercept and decipher sensitive information.
Data Validation and Sanitization
Input validation and sanitization are crucial for preventing vulnerabilities like SQL injection and cross-site scripting (XSS). Validating user inputs ensures that they adhere to predefined rules and formats. Sanitization removes potentially harmful characters or scripts from user inputs, preventing malicious code from being executed. These measures are fundamental in preventing attacks that leverage flawed input handling.
Secure Coding Practices for Sensitive Data
Robust coding practices are essential for handling sensitive data within APIs. Developers should adhere to strict guidelines for handling passwords, credit card information, and other sensitive data elements. Employing secure coding practices minimizes the risk of vulnerabilities that could be exploited to gain unauthorized access to sensitive information. This includes limiting access to sensitive data to only authorized personnel and employing parameterized queries to prevent SQL injection attacks.
Data should be handled with the utmost care to prevent vulnerabilities.
Data Masking and Tokenization
Data masking and tokenization are techniques used to protect sensitive data without removing it completely. Data masking replaces sensitive data with a non-sensitive representation, while tokenization substitutes sensitive data with unique, non-sensitive tokens. These techniques allow for testing and development without exposing real data, ensuring compliance with regulations. Data masking is often used in testing environments, allowing developers to simulate interactions with sensitive data without revealing real data.
Tokenization replaces sensitive data with unique, non-sensitive tokens that can be used to access the original data in a secure manner.
API Rate Limiting and Throttling
API rate limiting and throttling are crucial components of secure API integration. They protect APIs from abuse, ensuring fair access for all users and preventing denial-of-service attacks. Implementing these strategies safeguards API performance and maintains a positive user experience.Effective rate limiting and throttling are vital for managing the volume of requests an API receives. This prevents overwhelming the system and maintaining optimal response times for legitimate users.
By carefully managing request rates, APIs can maintain stability and reliability.
Purpose of Rate Limiting and Throttling
Rate limiting and throttling mechanisms control the frequency of API requests from a given source. This prevents malicious actors from overwhelming the API with excessive requests, which can compromise its performance and availability. They also help distribute resources fairly among multiple users.
Methods for Implementing Rate Limiting Strategies
Various techniques can be employed to implement effective rate limiting strategies. These techniques can be categorized based on their implementation approach and effectiveness.
- Fixed-Window Rate Limiting: This approach defines a specific time window (e.g., 1 minute) and allows a predefined number of requests within that window. Exceeding the limit results in throttling. This is a straightforward method for basic rate limiting. For example, a fixed-window approach might allow 100 requests per minute from a single IP address.
- Sliding-Window Rate Limiting: This technique uses a sliding window, continuously moving forward in time. This approach provides more flexibility than fixed-window limiting, as it considers requests over a more dynamic time frame. For example, a sliding window of 15 minutes might allow 1000 requests, with new requests added to the window and old ones removed. This ensures the system is responsive to changing usage patterns.
- Leaky Bucket Algorithm: This method envisions a bucket that fills with incoming requests. A constant leak rate drains requests from the bucket. If the bucket fills, new requests are dropped or queued until space becomes available. This algorithm is effective at handling bursts of requests while maintaining a steady flow. For instance, an API might have a bucket that allows 10 requests per second, with requests exceeding this rate being rejected or placed in a queue.
Advantages of Rate Limiting for API Security and Performance
Rate limiting significantly enhances API security by mitigating the risk of denial-of-service attacks. By limiting the rate of requests, the API becomes less vulnerable to overload and maintains stability. Moreover, rate limiting improves API performance by ensuring that legitimate users receive timely responses, minimizing delays.
Rate Limiting Techniques and Effectiveness
| Technique | Effectiveness | Description |
|---|---|---|
| Fixed-Window | Good for basic rate limiting | Simple to implement, but can be less adaptive to varying request patterns. |
| Sliding-Window | Better for dynamic usage | More adaptive to changing request patterns, better handling of bursts. |
| Leaky Bucket | Excellent for handling bursts | Handles bursts effectively and provides a steady flow of requests. |
Monitoring API Usage Patterns to Identify Potential Abuse
Regular monitoring of API usage patterns is essential to detect potential abuse. This includes analyzing request frequency, origin IP addresses, and request types. Tools and techniques are available to help identify unusual or suspicious patterns that might indicate malicious activity. By monitoring API usage, administrators can promptly address potential issues before they escalate.
Secure API Design Principles
Designing secure APIs is paramount for protecting sensitive data and ensuring reliable interactions. A robust API design considers various security aspects from the outset, preventing vulnerabilities that could compromise the system. This approach emphasizes proactive security measures rather than reactive fixes.Implementing these principles leads to a more resilient API ecosystem, reducing the risk of breaches and enhancing the overall user experience.
This involves not just technical considerations but also a comprehensive understanding of the potential threats and vulnerabilities inherent in API interactions.
Key Principles for Secure API Design
Fundamental principles underpin secure API design, guiding developers to create robust and trustworthy interfaces. These principles are critical for building APIs that are resistant to attacks and maintain user trust. Adherence to these principles is crucial to safeguarding sensitive data and preventing unauthorized access.
- Least Privilege Principle: APIs should only grant the minimum necessary permissions to perform specific tasks. This minimizes the potential impact of a security breach.
- Principle of Separation of Concerns: API functionality should be divided into distinct, manageable modules. This allows for targeted security controls and easier troubleshooting.
- Defense in Depth: Implement multiple layers of security controls to create a layered defense mechanism. This includes authentication, authorization, input validation, and more.
- Regular Security Audits: Regularly evaluate API security measures to identify vulnerabilities and address potential weaknesses. This proactive approach minimizes the impact of emerging threats.
Best Practices for API Documentation and Versioning
Clear and comprehensive documentation, coupled with a well-defined versioning strategy, are vital for secure API usage. This enables developers to understand and utilize the API effectively while ensuring compatibility across different versions.
- Detailed Documentation: API documentation should include comprehensive details about each endpoint, parameters, expected responses, and error handling mechanisms. This ensures that developers can understand and utilize the API properly.
- Versioning Strategy: A well-defined versioning strategy allows for the evolution of the API while maintaining compatibility with older versions. Clear versioning helps maintain a smooth transition between updates and avoids breaking existing integrations.
- API Versioning Examples: Examples of versioning include using a semantic versioning scheme (e.g., 1.0.0, 1.1.0) or specifying versions in the URL (e.g., /v1/users, /v2/users).
API Endpoints Requiring Protection
Certain API endpoints are more vulnerable and require enhanced security measures. Protecting these endpoints is crucial for safeguarding sensitive data and preventing unauthorized access.
- Sensitive Data Endpoints: Endpoints handling user data, financial transactions, or personal information require robust security protocols. These endpoints should employ encryption and secure authentication methods.
- Authentication and Authorization Endpoints: Endpoints responsible for verifying user identities and granting access to resources should be protected with strong authentication mechanisms.
- Admin Endpoints: Endpoints granting administrative privileges necessitate stringent access controls to prevent unauthorized modification of critical system settings.
Common API Vulnerabilities
Awareness of common API vulnerabilities is essential for building secure APIs. Understanding these vulnerabilities allows for the implementation of preventative measures.
- Injection Attacks: Injection vulnerabilities allow attackers to introduce malicious code into the API. These vulnerabilities often occur when user inputs are not properly sanitized.
- Broken Authentication: Weak or insecure authentication mechanisms enable unauthorized access to API resources. This can lead to data breaches and system compromises.
- Authorization Flaws: Insecure authorization mechanisms allow unauthorized users to access restricted resources. This can result in data leaks or system malfunctions.
- Security Misconfiguration: Improperly configured APIs can leave vulnerabilities open to exploitation. This can range from outdated libraries to insecure server configurations.
Role of Security Headers in Protecting APIs
Security headers play a critical role in enhancing the security posture of APIs. These headers provide additional layers of protection against various attacks.
- Content Security Policy (CSP): CSP headers restrict the resources that a web page or API can load, mitigating cross-site scripting (XSS) attacks. This prevents malicious scripts from executing on the client-side.
- Strict Transport Security (HSTS): HSTS ensures that connections to the API are always encrypted, enhancing the security of data transmission. This prevents man-in-the-middle attacks.
- X-Frame-Options: This header prevents clickjacking attacks, where a malicious website tries to embed the API in an iframe.
Implementing Secure API Integration in Different Environments
Secure API integration transcends the specific deployment environment. Maintaining robust security protocols is crucial, regardless of whether the API is hosted in the cloud, on-premises, or a hybrid model. This section explores the unique security considerations for each deployment scenario.
Secure API Integration in Cloud Environments
Cloud providers like AWS, Azure, and GCP offer various services for API deployment and management. Leveraging these services can significantly streamline security implementation. Key considerations include employing managed identity services for authentication, utilizing cloud-native firewalls for network security, and adopting cloud-based encryption tools for data protection. The inherent scalability and elasticity of cloud environments are essential for handling fluctuating API traffic demands while maintaining security posture.
Cloud-based security tools and frameworks automate many security tasks, reducing operational overhead.
Secure API Integration in On-Premise Deployments
On-premises deployments require a more hands-on approach to security. Careful configuration of firewalls, intrusion detection systems (IDS), and access control lists (ACLs) is essential. Data encryption at rest and in transit is paramount. Regular security audits and vulnerability assessments are vital to identify and mitigate potential risks. Implementing robust security protocols from the outset, including multi-factor authentication (MFA), is critical to maintaining a strong security posture.
Thorough documentation of security configurations is crucial for maintaining consistency and auditability.
Securing APIs in Hybrid Environments
Hybrid environments combine on-premises and cloud-based resources. Security in such environments demands careful consideration of the unique challenges. Establishing secure communication channels between on-premises and cloud components is vital. Ensuring consistent security policies across both environments is critical. Implementing strong authentication and authorization mechanisms that seamlessly integrate across both environments is essential.
Regular security monitoring and auditing across all components are paramount to maintain a holistic view of the security posture.
Comparison of Secure API Implementation Strategies
| Environment | Authentication | Authorization | Data Security | Network Security |
|---|---|---|---|---|
| Cloud (AWS/Azure/GCP) | IAM Roles, Managed Identities | RBAC, API Gateway Policies | Cloud-native encryption, Data Loss Prevention | Cloud Firewalls, Network Security Groups |
| On-Premise | Active Directory, LDAP | Role-based access control, ACLs | Hardware-based encryption, Network segmentation | Firewall, Intrusion Detection/Prevention System |
| Hybrid | Federated Identity, Hybrid Authentication | Combined Authorization Mechanisms | Hybrid Encryption Strategies, Data Loss Prevention | Secure VPNs, Hybrid Networking |
Leveraging Security Tools and Frameworks
Specific security tools and frameworks can significantly enhance API security across different environments. For instance, using API gateways (e.g., Kong, Apigee) for rate limiting, authentication, and authorization can enhance security in cloud deployments. For on-premises deployments, using intrusion detection and prevention systems (IDS/IPS) can proactively identify and mitigate potential threats. Implementing security information and event management (SIEM) systems can provide a central point for monitoring security events across hybrid environments.
Thorough testing and continuous monitoring are critical to identify and address potential vulnerabilities.
Monitoring and Auditing API Activity
Robust monitoring and auditing of API activity is crucial for maintaining API security and performance. This involves systematically tracking API calls, identifying potential issues, and facilitating swift responses to security incidents. Proactive monitoring allows for early detection of anomalies, ensuring the API continues to function reliably and securely.Effective monitoring of API activity involves more than just basic logging.
It necessitates a comprehensive approach that encompasses both performance metrics and security-related data. This allows for a holistic understanding of API health and identifies potential vulnerabilities.
Importance of Logging and Monitoring API Calls
Comprehensive logging of API calls provides critical insights into API usage patterns, performance bottlenecks, and potential security breaches. Detailed logs record timestamps, request parameters, response codes, and other relevant information, offering a historical record of API interactions. This data is invaluable for debugging issues, identifying trends, and evaluating the overall health of the API.
Examples of Tools for Monitoring API Performance and Security
Numerous tools are available for monitoring API performance and security. These tools often offer features like real-time monitoring dashboards, detailed logging, and automated alerts. Popular options include:
- APIMatic: This platform provides comprehensive API monitoring capabilities, including performance tracking, security auditing, and analytics. It offers insights into API usage patterns and helps identify potential performance bottlenecks.
- Postman: While primarily known as an API client, Postman also offers features for monitoring API performance. Its integrations with other monitoring tools allow for a more holistic approach to API management.
- Grafana: This open-source tool excels at visualizing data from various sources, including API logs. Its flexibility allows for custom dashboards tailored to specific monitoring needs.
Implementing Security Auditing for API Usage
Security auditing for API usage involves meticulously tracking API activities to detect and prevent security threats. This includes recording user authentication details, API endpoints accessed, and data exchanged. Implementing granular logging across different API endpoints is essential for effective security auditing. Security audits should be configured to capture sensitive data, such as access tokens and API keys, without compromising security.
Table of Tools for API Monitoring and Security Auditing
The following table provides a summary of common tools for monitoring and security auditing API activity.
Secure API integration is crucial for robust mobile applications. A well-designed API is essential for a smooth user experience in mobile app development, especially when dealing with sensitive data. For instance, proper authentication and authorization protocols are vital for ensuring the safety and integrity of the data flowing between the app and the server. This secure integration process is a key consideration in the entire mobile app development lifecycle, impacting the overall security posture of the application.
| Tool | Primary Function | Strengths |
|---|---|---|
| APIMatic | Comprehensive API monitoring | Performance tracking, security auditing, analytics |
| Postman | API client, performance monitoring | Easy-to-use interface, integrations with monitoring tools |
| Grafana | Data visualization | Customizable dashboards, integrates with various data sources |
| Elasticsearch, Logstash, Kibana (ELK Stack) | Centralized logging and analysis | Scalable, powerful search and analysis capabilities |
Identifying and Responding to Security Incidents Related to API Integration
A well-defined incident response plan is critical for managing security incidents related to API integration. This plan should Artikel procedures for identifying, containing, and resolving security breaches. Key elements of the plan include:
- Alerting Mechanisms: Implementing systems to promptly alert security personnel of suspicious activity.
- Investigation Protocols: Establishing clear procedures for investigating reported security incidents.
- Mitigation Strategies: Developing strategies to contain and mitigate the impact of security incidents.
A robust incident response plan is essential for minimizing the impact of security breaches and maintaining the integrity of the API. This should include communication channels and roles for effective response to potential security breaches.
Secure API Integration in Microservices Architecture
Microservices architecture, characterized by its modularity and scalability, presents unique security challenges when integrating APIs. Ensuring secure communication and data integrity across numerous independent services requires a robust strategy encompassing authentication, authorization, and data protection mechanisms. This approach must be adaptable to the dynamic nature of microservices environments.Implementing secure API integration in a microservices ecosystem requires careful consideration of the communication protocols, data formats, and security measures in place to safeguard sensitive information.
This is especially crucial in distributed systems where multiple services interact.
Challenges of Secure API Integration in Microservices
The distributed nature of microservices architecture introduces specific security challenges. Maintaining consistent security policies across diverse services and ensuring secure communication between them can be complex. Managing authentication and authorization for numerous services, each with its own potentially unique requirements, is a significant undertaking. The sheer number of potential points of failure in a microservices environment increases the attack surface, necessitating robust security measures at every layer.
Secure Communication Between Microservices
Secure communication between microservices is critical for preventing unauthorized access and maintaining data integrity. Employing encryption protocols, such as TLS/SSL, for all inter-service communication is paramount. This ensures that data exchanged between services remains confidential and prevents eavesdropping. Implementing proper authentication mechanisms at the service boundaries is essential to verify the identity of requesting services. Using API keys, JWT tokens, or other appropriate methods are critical for verifying the identity of each request.
Service Discovery and Security in Microservices, Secure API integration
Effective service discovery is crucial for secure API integration in a microservices environment. Service discovery mechanisms provide the necessary context for identifying and locating available services. Robust service discovery solutions are needed to handle the dynamism of microservices deployments and should include security considerations. Service discovery systems need to be secured themselves, to prevent unauthorized access to the service registry.
Security measures for the service registry must be robust and align with the overall security strategy.
Security Best Practices for Microservices APIs
Implementing security best practices for microservices APIs is essential for maintaining the integrity and confidentiality of data. Implement strict access control lists (ACLs) for each API endpoint to control the services that can access it. Utilize API gateways to enforce these policies and act as a single point of entry for all external requests. Regularly update and patch services to address known vulnerabilities is essential.
Logging and monitoring API activity are crucial for detecting and responding to security incidents. Implement comprehensive logging of all API interactions to facilitate auditing and debugging.
Design for a Secure API Gateway in Microservices Architecture
A secure API gateway acts as a central point of entry for all external requests to the microservices ecosystem. It performs tasks like authentication, authorization, rate limiting, and transformation. A well-designed gateway should include features like:
- Authentication and Authorization: The gateway should handle authentication and authorization, verifying the identity of clients before routing requests to the appropriate microservices. This process can use industry standard methods like OAuth 2.0.
- Rate Limiting and Throttling: The gateway can implement rate limiting and throttling to prevent abuse and protect microservices from overload. This is particularly important when handling high volumes of traffic.
- API Transformation and Mediation: The gateway can transform requests and responses to accommodate varying service protocols and data formats. This helps to maintain consistency across different services.
- Security Monitoring and Logging: The gateway should collect and log all API activity to aid in monitoring and auditing, including access attempts, errors, and successful requests.
A secure API gateway ensures consistent security policies across all services and provides a centralized point for managing access to microservices.
Secure API Integration Best Practices and Standards
Implementing secure APIs requires adherence to industry best practices and standards. This involves understanding the nuances of various compliance requirements, security certifications, and the importance of regular security assessments. A robust security posture is crucial for maintaining trust, preventing breaches, and ensuring the integrity of data exchanged through APIs.
Industry Standards for Secure API Design
Industry standards, like those from the OpenAPI Initiative (formerly Swagger), define best practices for API design, fostering interoperability and security. These specifications emphasize the use of well-defined structures for requests and responses, enabling clear communication and reducing ambiguity. Standardized protocols, such as HTTPS, are fundamental for securing communication between clients and APIs. Clear documentation, outlining API endpoints, parameters, and authentication mechanisms, is vital for developers and security personnel alike.
The OWASP API Security Top 10 project provides a valuable resource for identifying potential vulnerabilities and recommending mitigation strategies.
Compliance Requirements for Secure API Integration
Meeting compliance regulations is paramount in many sectors. For instance, HIPAA mandates strict data security measures for healthcare APIs, while PCI DSS dictates specific requirements for handling financial data. Other regulations, like GDPR, demand transparent data handling practices and user consent mechanisms. Understanding and adhering to these regulations ensures legal compliance and protects sensitive data. Failure to comply can result in substantial penalties and reputational damage.
Security Certifications for APIs
Several security certifications validate the implementation of secure API practices. OWASP (Open Web Application Security Project) provides resources and guidelines for API security. ISO 27001, a widely recognized standard for information security management systems, can be adopted for robust API security implementation. Other industry-specific certifications, such as SOC 2, may also be relevant depending on the sector and the nature of the data being handled.
These certifications demonstrate a commitment to security and bolster trust in the API.
Significance of Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are crucial for identifying vulnerabilities in API integration. These assessments simulate real-world attacks, helping to pinpoint potential weaknesses before they are exploited. Penetration testing, performed by experienced security professionals, can reveal weaknesses in authentication, authorization, data validation, and other critical areas. The insights gained from these assessments allow for proactive mitigation of vulnerabilities, strengthening the overall security posture of the API.
Secure API Integration Resources
Numerous resources offer guidance on secure API integration. The OWASP API Security Top 10 project provides a valuable list of common vulnerabilities and mitigation strategies. Organizations like NIST (National Institute of Standards and Technology) offer comprehensive frameworks for secure development practices, applicable to API design and implementation. Security blogs, articles, and forums offer additional insights and best practices.
Staying informed through these resources is essential for maintaining a robust security posture.
Final Review
In conclusion, implementing secure API integration is paramount for building robust and trustworthy applications. By understanding and applying the principles Artikeld in this guide, developers can significantly enhance the security posture of their APIs and protect sensitive data. This guide provides a practical roadmap to building secure APIs across various scenarios, ensuring your applications are safe and reliable.
FAQ Overview
What are the common security vulnerabilities in APIs?
Common API vulnerabilities include injection flaws, broken authentication, sensitive data exposure, missing authorization, and security misconfigurations. Understanding these risks is crucial for developing secure APIs.
How does rate limiting enhance API security?
Rate limiting prevents abuse and denial-of-service attacks by restricting the number of requests an API can handle within a specific timeframe. This helps maintain API performance and security.
What are the different types of authentication methods for APIs?
Common authentication methods include API keys, OAuth 2.0, and JSON Web Tokens (JWT). Each method has its strengths and weaknesses, and the optimal choice depends on the specific security requirements of the application.
What is the role of API gateways in secure API integration?
API gateways act as a central point for managing and securing API traffic. They enforce authentication, authorization, and rate-limiting policies, protecting the underlying APIs from malicious requests.